Microsoft Office reports including built-in macros can be dangerous. Macros are essentially bits of computer code, and historically they’ve been vehicles for malware. Luckily, modern versions of Office contain security features that will protect you from macros.
Macros are still potentially dangerous. But, like a lion at the zoo, you’d have to go out of your way to be worried by them. As long as you don’t bypass the built-in security features, you shouldn’t have to worry.
What’s a Macro?
Microsoft Office records — Word, Excel, PowerPoint, and other types of documents — can contain embedded code written in a programming language known as Visual Basic for Applications (VBA).
You can record your own macros using the built-in Macro Recorder. This allows thou to automate repeated assignments — in the future, you’ll be able to repeat the actions you recorded by running the macro. Follow our guide to creating Excel macros for more information. Macros you’ve created yourself are fine and don’t pose a security risk.
Still, wicked people could write VBA code to create macros that do bad things. They could then embed these macros in Office reports and distribute them online.
Why Can Macros Do Potentially Dangerous Things?
You might consider that a programming language created to automate tasks in an Office suite would be fairly simple, but you’d be wrong.
For example, macros can use the VBA SHELL ability to run random commands and programs or use the VBA KILL ability to delete files on your hard drive.
After a malicious macro is loaded into an Office application like Word via an infected document, it can use features like “AutoExec” to automatically start with Word or “AutoOpen” to automatically run whenever you open a document. In this way, the macro virus can integrate itself into Word, infecting future documents.
You might wonder why such harmful behavior is even possible with an Office suite. VBA macros were added to Office in the 90s, at a time when Microsoft wasn’t serious about security and before the Internet brought the threat of harmful macros home. Macros and VBA code weren’t planned for confidence, just like Microsoft’s ActiveX technology and many of the points in Adobe’s PDF Reader.

Macro Viruses In Action
As you might expect, malware authors took advantage of such insecurities in Microsoft Office to create malware. One of the most well-known is the Melissa virus from 1999. It was scattered as a Word text holding a macro virus. When opened with Word 97 or Word 2000, the macro would execute, gather the first 50 entries in the user’s address book, and email a copy of the macro-infected Word document to them via Microsoft Outlook. Many recipients would open the infected document and the cycle would continue, clogging email servers with an exponentially increasing amount of junk mail.
Other macro viruses have caused trouble in other ways — for example, the Wazzu macro virus infected Word documents and tampered with them by occasionally moving words around inside the document.
These macros were much more trouble when Office trusted macros and loaded them by default. It no longer does.
These macros were much more trouble when Office trusted macros and loaded them by default. It no longer does.
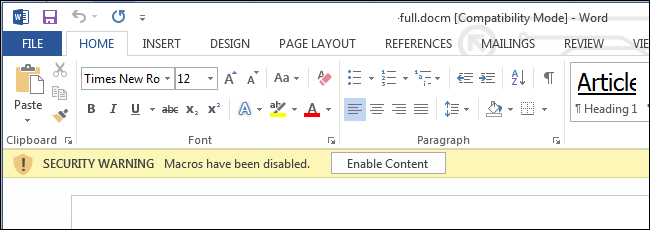
How Microsoft Office Protects Against Macro Viruses
Thankfully, Microsoft eventually got serious about security. Office 2003 added a macro security level feature. By fault, single macros signed with a taken certificate could run.
Modern versions of Microsoft Office are even more restrictive. Office 2013 is set to disable all macros by default, providing a notification that the macro wasn’t allowed to run.

Since Office 2007, Macros are also much easier to detect. By error, official Office documents are saved with the “x” addition. For example, .docx, .xlsx, and .pptx for Word, Excel, and PowerPoint documents. Documents with these file extensions are not allowed to contain macros. Only papers including a file extension ending with “m” — that’s .docm, .xlsm, and .pptm — are admitted to contain macros.
How to Protect Yourself
To actually be infected, you’d have to download a file containing a malicious macro and go out of your way to disable Office’s built-in security features. As a consequence of this, macro infections are now much less constant.
Here’s all you need to do: Only run macros from people or organizations you trust when you have a good reason to do so. Don’t disable the built-in macro security features.




Post A Comment:
0 comments: